
Official I Identify As A Threat My Pronouns Are Try Me Shirt, hoodie
What is threat modeling? Threat modeling is a proactive strategy for evaluating cybersecurity threats. It involves identifying potential threats, and developing tests or procedures to detect and respond to those threats. This involves understanding how threats may impact systems, classifying threats and applying the appropriate countermeasures.
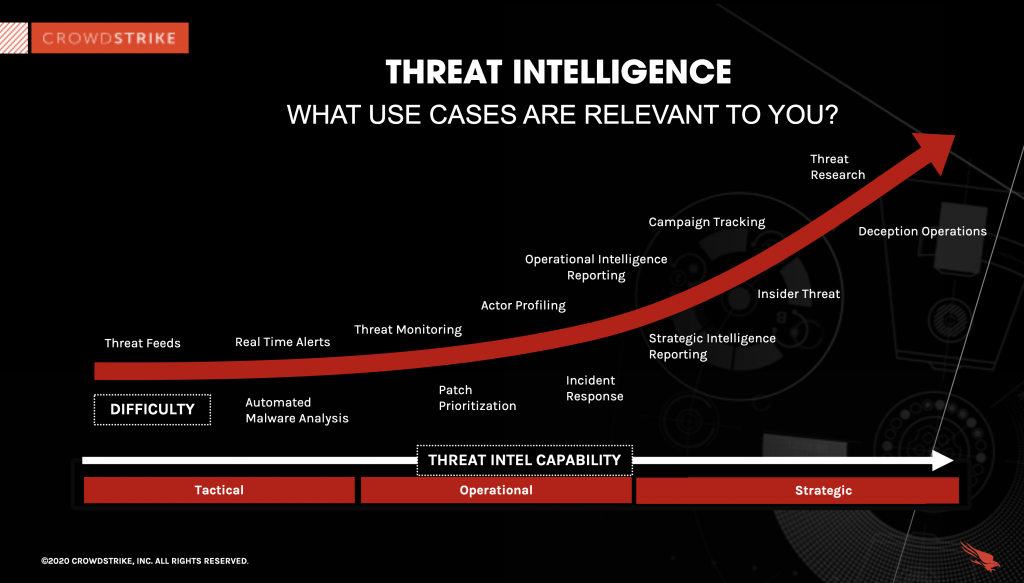
What is Cyber Threat Intelligence? [Beginner's Guide] (2023)
The goal of the threat categorization is to help identify threats both from the attacker and the defensive perspective . DFDs produced in step 1 help to identify the potential threat targets from the attacker's perspective, such as data sources, processes, data flows, and interactions with users. These threats can be classified further as the.

I Identify As A Threat Pronouns Are Try Me Shirt
Identify Risk Assessment Identify threats to organizational assets (both internal and external) adversary Identify providers of threat information NIST SP 800-53 Rev. 4 PM-16 ISO/IEC 27001 A.13.1.2 Allows the organization to identify current known IP addresses for servers and block inbound and outbound connections to this source.

I Identify As A Threat Pronouns Are Try Me Shirt
Detecting. Insider Threat Indicators. Venu Shastri - July 22, 2022. Cybersecurity is an absolute necessity in today's networked world, and threats have multiplied with the recent expansion of the remote workforce. Hackers and cybercriminals who gain access to IT assets can seriously harm your organization's operations, finances, reputation.

i identify as a threat my pronouns are try me shirt
1. Insider threats An insider threat occurs when individuals close to an organization who have authorized access to its network intentionally or unintentionally misuse that access to negatively affect the organization's critical data or systems. This article is part of What is incident response? Plans, teams and tools Which also includes:
I identify as a threat
To identify threats, you can use SWOT analysis, PESTLE analysis, scenario planning, risk assessment, and feedback. SWOT analysis evaluates strengths and weaknesses while PESTLE analysis examines.
How To Identify Unseen Threats
A1: Threats are identified as part of the national security planning process and reflected in guidance documents drafted at the outset of a new administration, including the National Security Strategy (NSS) and National Defense Strategy (NDS).
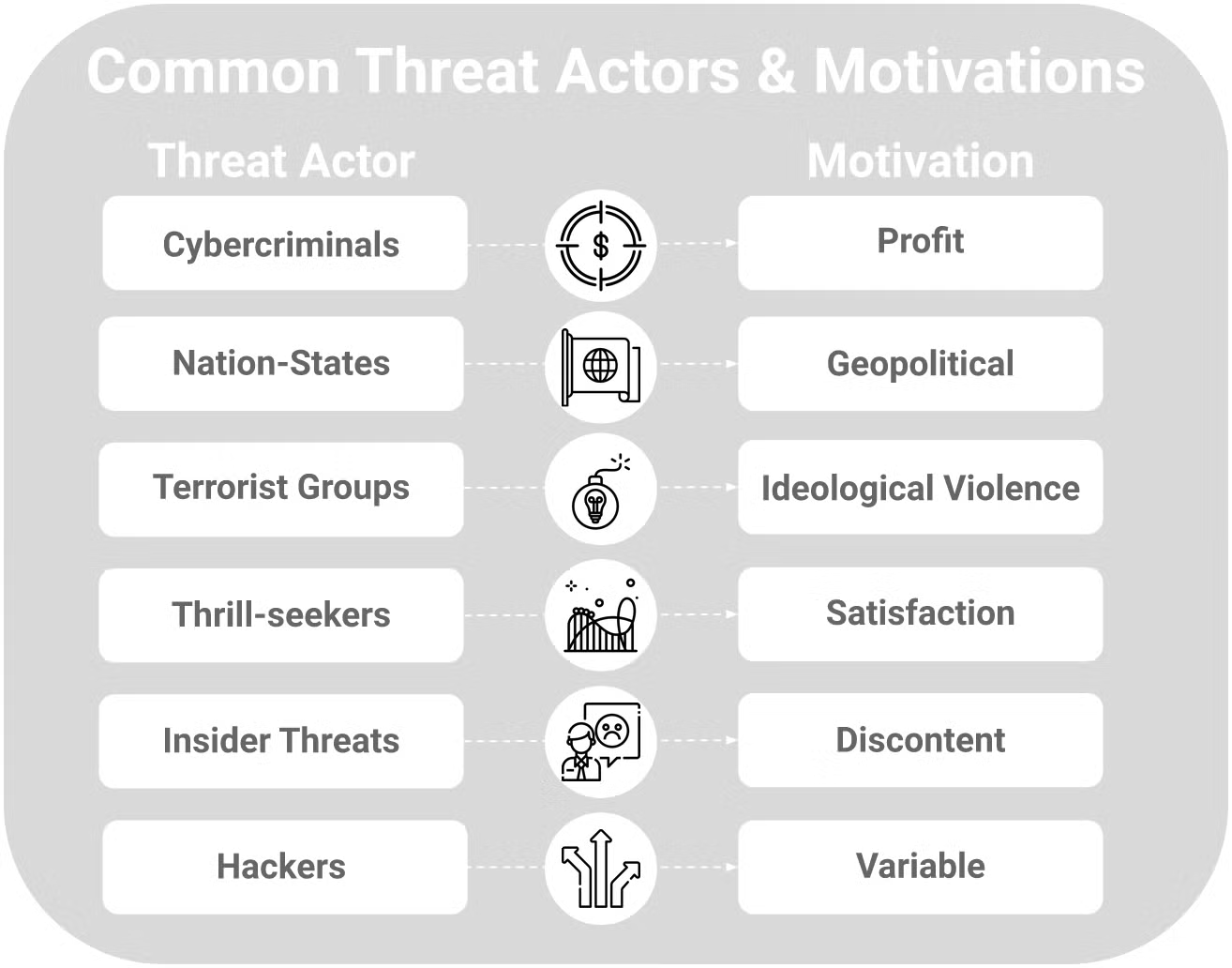
What is a Threat Actor? Types & Examples of Cyber Threat Actors
Much like software bugs, the earlier you identify threats, the more cost effective it is to address them. A threat model is a living document and should continue to evolve as your workloads change. Revisit your threat models over time, including when there is a major change, a change in the threat landscape, or when you adopt a new feature or.

"What do you identify as? A THREAT" Sticker for Sale by heatherharris11
Any cyber-attack, no matter how small, is a threat to our national security and must be identified, managed, and shut down. CISA's Role. CISA diligently tracks and shares information about the latest cybersecurity risks, attacks, and vulnerabilities, providing our nation with the tools and resources needed to defend against these threats.

I Identify As A Threat Pronouns Are Try Me Shirt
For several weeks, threat actors have been targeting insecure Microsoft SQL database servers (MSSQL) of organizations based in the U.S., EU and Latin America, in order to deploy ransomware. In the ongoing campaign, observed by researchers with Securonix, attackers first brute force administrative passwords on MSSQL servers in order to download.

I identify as a threat. My pronouns are try /me iFunny
Itemizing your application's important characteristics and actors helps you to identify relevant threats during step 4. Step 3: Decompose your application. A detailed understanding of the mechanics of your application makes it easier for you to uncover more relevant and more detailed threats. Step 4: Identify threats.

I Identify as A Threat My Pronouns Are Try Me Patch Etsy Australia
The report considers the four major types of attacks: evasion, poisoning, privacy and abuse attacks. It also classifies them according to multiple criteria such as the attacker's goals and objectives, capabilities, and knowledge. Evasion attacks, which occur after an AI system is deployed, attempt to alter an input to change how the system.

I Identify as a Threat Pronouns Are Try Me Snarky Shirt Etsy
An insider threat is a cybersecurity risk that comes from within the organization — usually by a current or former employee or other person who has direct access to the company network, sensitive data and intellectual property (IP), as well as knowledge of business processes, company policies or other information that would help carry out such a.

"Pronoun Humor I identify as a threat my pronouns are try/me
Protect your people from email and cloud threats with an intelligent and holistic approach. Change User Behavior. Help your employees identify, resist and report attacks before the damage is done. Combat Data Loss and Insider Risk. Prevent data loss via negligent, compromised and malicious insiders by correlating content, behavior and threats.
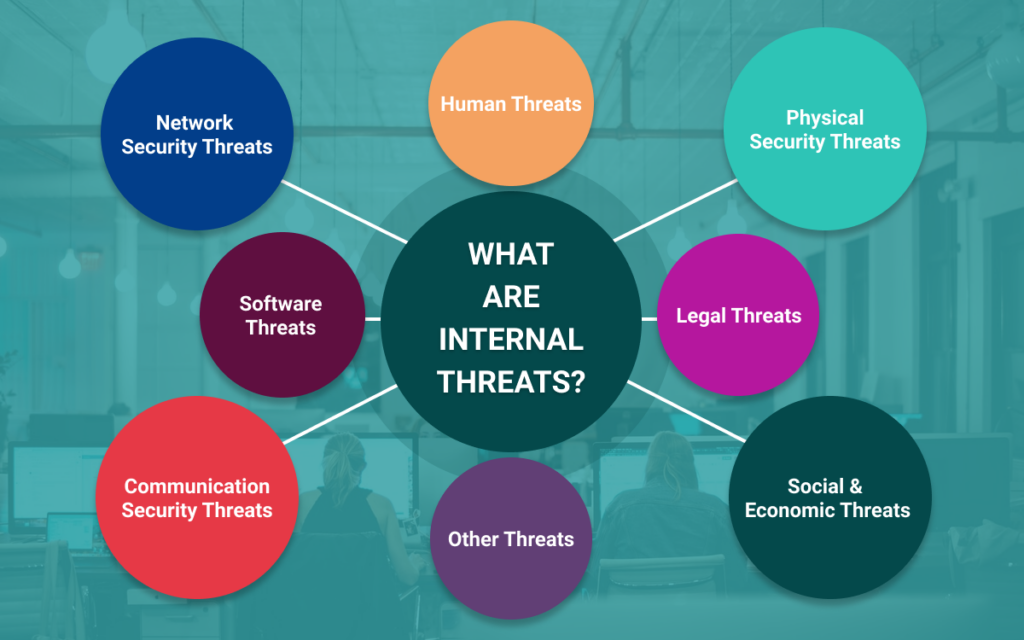
Internal Vs External Threats Here’s All You Need to Know Secure Triad
Identity threat detection and response (ITDR) is a security procedure for identifying, reducing, and responding to potential identity-based threats, such as compromised user accounts, leaked passwords, data breaches, and fraudulent activity.These identity-based attacks pose serious threats to organizational security. In this article, we'll shed some light on ITDR, the security challenges it.

I identify as a threat my pronouns are try me funny Tshirt
What is a threat? In cybersecurity, the most common definition of a threat is this: Anything that could exploit a vulnerability, which could affect the confidentiality, integrity or availability of your systems, data, people and more.